Automated Ransomware Recovery Assurance for AWS Cloud Backups
Automated Ransomware Recovery Assurance for AWS Cloud Backups
Key Capabilities
- Continuous Data Integrity Validation for AWS Services
Elastio integrates with Amazon S3, EBS Snapshots, AWS Backup, AWS DRS, and more to continuously inspect recovery points for ransomware encryption and corruption, at scale and with zero performance impact - 99.999% Precision Ransomware Detection
Elastio’s ML engine, trained through reverse engineering every significant ransomware strain since 2014, detects encryption with 99.999% accuracy – including polymorphic ransomware, fileless malware, and stealthy low-rate encryption that evades traditional tools. - Audit Reporting for Compliance and Insurance
Elastio delivers compliance-grade evidence to support frameworks such as NIST, DORA, NYDFS, and cyber insurance underwriting.
Executive Summary
Today, ransomware resilience isn’t just best practice – it’s required. Regulators, insurers, and your board expect proof that you can recover from an attack, without delays or surprises.
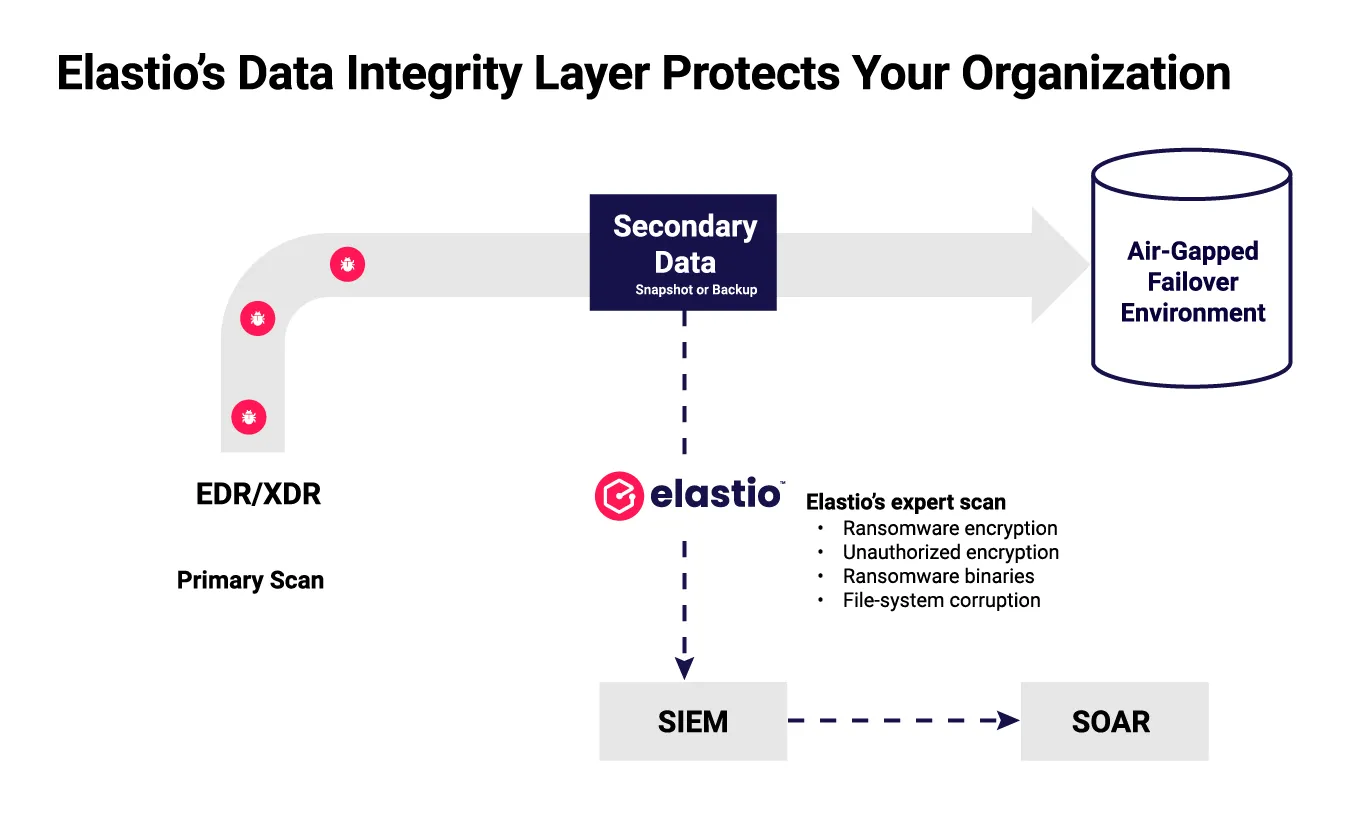
For businesses on AWS, taking backups alone isn’t enough. Ransomware can encrypt data before it’s detected, and those compromised files often end up silently stored in backups. Without validation, there’s no guarantee your recovery points are safe.
Elastio + AWS: Built-In Confidence
Elastio integrates with AWS Backup, AWS Elastic Disaster Recovery, AWS Logically Air-Gapped Vaults, and AWS Restore Tests to automatically scan backups and replicated data for signs of ransomware, insider threat encryption, and data corruption. No added complexity. Just assurance that your recovery points will be safe to use when you need them the most.
The Problem: Ransomware Has Evolved – Your Recovery Strategy Must Too
Today’s ransomware is no longer loud, obvious, or easy to spot. Adversaries use sophisticated tactics to compromise your data and backup sets silently:
- Fileless malware executes in memory, leaving no traditional footprint for antivirus or malware scanners to catch.
- Polymorphic ransomware constantly changes its signature to evade detection.
- Living-off-the-land (LOTL) techniques use native tools (like PowerShell or bash) to blend in with normal operations.
- Low-and-slow encryption keeps activity below detection thresholds – only small chunks of data are encrypted at a time to avoid triggering alerts.
These techniques allow ransomware to evade endpoint protection, bypass SIEM alerts, and infect backups – often weeks before discovery. When the time comes to restore, you may be reaching for data that’s already compromised.
The Solution: Elastio + AWS = Assured Recovery
Elastio closes the ransomware recovery gap by validating the integrity of your AWS-based backups and replicas.
By combining Elastio’s ML-powered data integrity scanning with AWS’s proven data protection services, you get:
- Continuous, out-of-band scans for ransomware encryption and data corruption
- Proven-clean recovery points you can trust
- Compliance-aligned reporting for regulatory and insurance needs
AWS provides the foundation:
- AWS Backup for centralizing and automating data protection
- AWS Elastic Disaster Recovery (DRS) for low-RTO failover
- AWS LAG Vaults for secure, immutable storage
- AWS Restore Tests for simulated recovery
Elastio validates each one by ensuring the data is clean.
“Elastio allowed us to see almost immediately which backups were clean. That saved us days—possibly weeks—of trial and error.”
— Jeff Fudge, Director of Cloud Solutions, JetSweep
How it Works
- Deploy easily: Elastio launches via CloudFormation.
- Scan Intelligently: Elastio scans AWS backups, DRS replicas, and snapshots for ransomware, insider threat, encryption, and data corruption.
- Certify Recovery Points: Each clean recovery point is tagged and tracked with a “Last Known Clean” badge and a forensic report.
- Recover Confidently: When disaster strikes, your team knows exactly which backup is safe to restore from.
Why Elastio + AWS
- AWS Storage & Security Competency Partner listing; transactable via AWS Marketplace.
- Broad Service Coverage – EC2, EBS, EFS, S3, FSxN, ECS, EKS, AWS Backup, DRS, LAG Vaults, and more.
- Built for Zero-Trust – Out-of-band architecture means attackers inside the OS cannot tamper with scans or reports.
“Our primary focus was to fortify our backup system, ensuring improved mission-critical data recoverability and business continuity, particularly in the event of potential ransomware attacks. Elastio understood our priorities and collaborated with us in constructing a robust framework for a resilient and secure foundation for our data management needs.”
— Sanjay Singh, Head of DevSecOps, Games24x7
Ready to Prove Recovery?
Don’t let ransomware follow you to the cloud.
With AWS and Elastio, cloud transformation includes provable ransomware recovery, so you can scale securely, recover confidently, and comply continuously.
Prove Recovery. Stop Ransomware.
Learn more:
Elastio Partnerships